TCP/IP is one of the most common suite of networking protocols used. This was first proposed in an RFC in 1989.
RFC or request for comment are documents containing methods, innovations, protocols, etc related to the internet. These RFCs may or may not be accepted as a standard.
In this blog, we’ll have a look at some of the common protocols which make up the TCP/IP model, the different layers of the TCP/IP model, and how data passes through each layer
Some common protocols in TCP/IP stack
The following protocols are a part of the TCP/IP suite of protocols that enable two or more machines (mostly Linux servers) to interact with each other. These protocols are
TCP: Transmission Control Protocol
TCP is a connection-oriented protocol. That is, it ensures that there is no data loss in transmission and that all the packets are transmitted in order.
In TCP the data to be transmitted is forwarded to the operating system by the application. The OS then converts the data into a suitable format.
This data then arrives at the destination machine. Here the data is arranged in order and any missing data is requested again.
Once all the data is received and arranged in proper order, it is forwarded to the application on the destination machine.
UDP: User Datagram Protocol
UDP is a connectionless protocol. Unlike TCP it does not guarantee the data to be present in the correct order nor does it promise data loss.
It, therefore, saves the time spent in arranging the data in proper order and re-transmission of the lost packets making it faster than TCP.
ICMP: Internet Control Message Protocol
Unlike TCP and UDP, ICMP is not an end-user protocol. That is, it is not used to transfer data or messages across the network.
Rather it is a control protocol used by different components of a network to check for errors in the network. This protocol works on the network layer of the OSI model.
IGMP: Internet Group Management Protocol
IGMP controls the behavior of machines during IP multicast.
Hardware Protocols
Hardware protocols describe how data will be transferred between different hardware components. Most of these protocols are packet-oriented.
That is, they divide the data into small packets and then transmit those packets out. The maximum packet size that TCP/IP supports is 64KB.
However, in reality, the packet size is far less than this because of the hardware limitations of the ethernet cable. It is generally 1500 bytes.
TCP / IP Model
TCP/IP Model is a simpler version of the OSI model. It is the most commonly used networking model.
Each piece of data has to pass through these four layers of the model. At each subsequent layer, additional information is added to the original data.
This additional information is added in the form of a header.
TCP/IP Model has four layers.
To understand it better, let’s dive into what these layers are and what do they do.
Application layer
This is the only layer visible to a user. Different applications which are used to send data, like the web browser, reside on this layer.
Also, a large number of protocols like HTTP, SMTP, and FTP reside on this layer.
At this layer, the data is all there is. No header exists here.

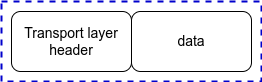
Transport layer
The raw data from the application layer is passed on to the transport layer. This layer takes care of delivering data to the correct process on the destination machine.
For example, if a request was sent from chrome, then the transport layer ensures that the response reaches chrome and not firefox.
The other purpose of this layer is to organize data packets and ensure that no data is lost during the transmission.
A header is added to the data sent down from the application layer. This header consists of
- Source port number
- Destination port number
- TCP flags like ACK, and SYN
The port numbers help identify the source and destination processes. The flags, on the other hand, help keep a track of the lost packets and help arrange them in order.
The combined unit of data – the body (sent down from the application layer) and the header is called a segment.
An interesting point to note here is the use of ACK flags. Now, all the TCP segments have an ACK flag set, except the first one.
This helps distinguish incoming requests (without an ACK) from the response of outgoing ones (when they come back, they’ll have ACK and are therefore allowed to pass)
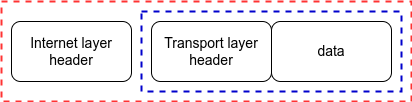
Internet Layer / IP layer
The internet layer is responsible for sending and receiving data packets. Once the internet layer receives a segment from the transport layer, it treats the entire segment as a body and adds another header to it.
The IP header along with the segment then forms a packet.
The IP layer adds the following headers to the segment
- Source IP address
- Destination IP address
- IP protocol being used, like ICMP, or IGMP
- IP option fields
If the packet size is too large, the internet layer divides it into smaller fragments before passing them over to the network access layer
Network access layer
The network access layer is where the actual transmission of data between two machines takes place. This involves the hardware components of the stack.
All the other layers reside within the OS kernel except the network access layer.
The packet received from the internet layer is appended with a header before sending it further to the other machine.
The following headers are added in this layer
- Source MAC / ethernet address
- Destination MAC / ethernet address
- Type of packet, eg IP packet
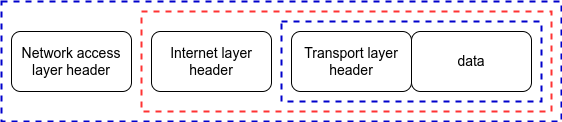
Once this is transmitted to the other machine, the reverse process takes place. That is, the network access layer of the other machine does the processing and removes its header.
It then passes the packet to the internet layer which will remove its header and pass the resulting segment to the transport layer.
The transport layer, after removing its header passes the data to the respective process which would then process this data as per the requirement